The practice of safeguarding and sending data and information in a format that only authorized parties can comprehend is known as cryptography. To guard against viruses or cyber attacks, encryption methods encode the original communication using crypto-mathematical ideas and rule-based calculations known as algorithms.
The term is derived from the Greek word “Kryptos,” which means secret or ‘hidden.’ Cryptography literally translates to “secret writing.” It derives from the science of cryptology, the art of deciphering and deciphering codes such as ancient hieroglyphics.
Data encryption is a critical tool for developing secure communications, networks, and system infrastructure. By adhering to the fundamentals of
Data encryption is a critical tool for developing secure communications, networks, and system infrastructure. Cryptography ensures that no unauthorized parties or threat actors can access confidential data by adhering to the pillars of information security. It is a highly specialized sector of cybersecurity that must be implemented by experts. Cryptography secures sensitive data in every part of our life, from web browsing to emailing to credit card or cryptocurrency transactions.
The best way to understand simple cryptography is to look at one of its earliest forms, the Caesar cipher. Julius Caesar used it to encrypt confidential correspondence between him and his officials.
Caesar encrypted his messages by changing the order of the alphabetical letters. In order to decrypt the message, the intended recipient would have to substitute the written letter for the corresponding letter in the original message to decode the encrypted message. This is called a substitution cipher.
We can break this description into two cryptographic elements: the algorithm and the key. The algorithm is simple and involves substituting a letter with another from later in the alphabet. The key is how many spots in the alphabet you must move to find the original letter or set of letters in a word to decrypt the message. The key was three in this version of Caesar cipher, in which case you would substitute the letter D for letter A, H for E, and so on.
Modern cryptography exists through the combination of advanced mathematics, computer science, communication, and engineering processes. Computers and operating systems use complex encryption methods to encode messages so only authorized parties can see them. The message, or plaintext, is converted into ciphertext using an encryption algorithm that generates an encryption key. In order to read the message, the recipient must use a decryption key, which turns the ciphertext back into plaintext.
Cryptographic algorithms (or ciphers) play a large role in data security because they are used to generate cryptographic keys and digital signatures, protect payment transaction protection, secure web browsing, and message authentication.
Cryptography And Its Application
The act of secret coding has been existing in the world for a long time, especially with the military, which uses some private communication pipelines to restrict the access of the masses from some “classified piece of information”.
Just as hidden languages are becoming obsolete, there is an evolution surrounding them lately. This concept is synonymous with cryptography, which is the process of studying secret communications in the trance of ensuring the information becomes inaccessible to a malicious third party.
Applied in different fields of endeavor, information is hidden by cryptography, with the use of encryption in a coded language that is foreign to easy accessibility of malicious third parties. So it simply keeps data safe and secure from an unauthorized user.
There are various applications of cryptography which are as follows −
Secrecy in Transmission − Some existing secrecy systems for transmission access a private key system for converting transmitted data because it is the quickest approach that functions with rational guarantee and low overhead.
If the multiple conversing parties is minute, key distribution is implemented periodically with a courier service and key preservation based on the physical security of the keys over the method of use and destruction after new keys are disseminated.
Secrecy in Storage − Secrecy in storage is frequently preserved by a one-key system where the user provides the key to the computer at the commencement of a session, and the system creates concerns of encryption and decryption during the phase of normal use.
Integrity in Transmission − Some users of communication systems are not as much worried about secrecy as about integrity. In a computer funds transfer, the sum sent from one account to another is usually public knowledge.
If an operating tapper can bring in a false transfer, funds can be shared illegally. An inaccuracy in an individual bit can cause millions of dollars to be wrongly credited or debited. Cryptographic methods are generally used to provide that intentional or accidental modification of transmitted data does not cause flawed actions to appear.
Integrity in Storage − The central meaning of assuring the integrity of accumulated data has previously been access control. Access control contains systems of locks and keys, guards, and other approaches of a physical or logical feature.
The recent advent of computer viruses has altered this to an important degree, and the use of cryptographic checksums for assuring the integrity of stored data is becoming broad.
Authentication of Identity − Authenticating the identity of individuals or systems to each other has been a difficulty for a very long time. Simple passwords have been used to test identity. More compound protocols such as the sequence of keywords exchanged between sets of parties are generally displayed in the movies or on television.
Credentialing Systems − A credential is generally a file that introduces one party to another by referencing a usually known trusted party. When credit is used, references are usually requested. The credit of the references is determined and they are contacted to discover the test of the applicant. Credit cards are generally used to credential an individual to achieve more credit cards.
Electronic Signatures − Electronic signatures are a means of monetary a lawfully binding transaction among two or more parties. It can be as functional as a physical signature, electronic signatures should be at least as hard to fake at least as simple to use, and accepted in a court of law as binding upon some parties to the operation.
The necessity for these electronic signatures is especially intense in business dealings wherein the parties to an agreement are not in a similar physical vicinity.
Encryption Algorithms, Decryption Algorithms, And Keys
Security is top of mind for anyone in IT these days. It must be, given that Gartner estimates that spending on information security and risk management will total $172 billion in 2022, up from $155 billion in 2021. While there are plenty of technologies you can buy to secure your data, encryption is one aspect of security technology that every computer user should understand.
Read Also: Cybercrime And Law Enforcement: Cooperation And Challenges
Encryption is a way for data—messages or files—to be made unreadable, ensuring that only an authorized person can access that data. Encryption uses complex algorithms to scramble data and decrypts the same data using a key provided by the message sender. Encryption ensures that information stays private and confidential, whether it’s being stored or in transit. Any unauthorized access to the data will only see a chaotic array of bytes.
Here are some essential encryption terms you should know:
- Algorithm
Also known as a cipher, algorithms are the rules or instructions for the encryption process. The key length, functionality, and features of the encryption system in use determine the effectiveness of the encryption.
- Decryption
Decryption is the process of converting unreadable ciphertext to readable information.
- Key
An encryption key is a randomized string of bits used to encrypt and decrypt data. Each key is unique, and longer keys are harder to break. Typical key lengths are 128 and 256 bits for private keys and 2048 for public keys.
There are two kinds of cryptographic key systems, symmetric, and asymmetric.
Symmetric Key Systems
In a symmetric key system, everyone accessing the data has the same key. Keys that encrypt and decrypt messages must also remain secret to ensure privacy. While it’s possible for this to work, securely distributing the keys to ensure proper controls are in place makes symmetric encryption impractical for widespread commercial use.
Asymmetric Key Systems
An asymmetric key system, also known as a public/private key system, uses two keys. One key remains secret—the private key—while the other key is made widely available to anyone who needs it. This key is called the public key. The private and public keys are mathematically tied together, so the corresponding private key can only decrypt that information encrypted using the public key.
Here’s an example of how encryption works with email-friendly software Pretty Good Privacy (PGP) or GnuPG—also known as GPG—for open-source aficionados. Say I want to send you a private message. I encrypt it using one of the programs listed below.
Here’s the message:
wUwDPglyJu9LOnkBAf4vxSpQgQZltcz7LWwEquhdm5kSQIkQlZtfxtSTsmawq6gVH8SimlC3W6TDOhhL2FdgvdIC7sDv7G1Z7p
CNzFLp0lgB9ACm8r5RZOBiN5ske9cBVjlVfgmQ9VpFzSwzLLODhCU7/2THg2iDrW3NGQZfz3SSWviwCe7GmNIvp5jEkGPCG
cla4Fgdp/xuyewPk6NDlBewftLtHJVf=PAb3
Once encrypted, the message becomes a jumbled mess of random characters. But, equipped with the key I send you, you can decrypt it and find the original message:
Come on over for hot dogs and soda!
Whether it’s in transit like our hot dog party email or resting on your hard drive, encryption works to keep prying eyes out of your business—even if they happen to gain access to your network or system.
The technology comes in many forms, with key size and strength generally being the most significant differences in one variety to the next.
Common Encryption Algorithms
- 1. Triple DES
Triple DES was designed to replace the original Data Encryption Standard (DES) algorithm, which hackers eventually learned to defeat with relative ease. At one time, Triple DES was the recommended standard and the most widely used symmetric algorithm in the industry.
Triple DES uses three individual keys with 56 bits each. The total key length adds up to 168 bits, but experts would argue that 112-bits in key strength is more accurate. Despite slowly being phased out, Triple DES has, for the most part, been replaced by the Advanced Encryption Standard (AES).
- 2. AES
The Advanced Encryption Standard (AES) is the algorithm trusted as the standard by the U.S. Government and numerous organizations. Although it is highly efficient in 128-bit form, AES also uses keys of 192 and 256 bits for heavy-duty encryption purposes.
AES is largely considered impervious to all attacks, except for brute force, which attempts to decipher messages using all possible combinations in the 128, 192, or 256-bit cipher.
- 3. RSA Security
RSA is a public-key encryption algorithm and the standard for encrypting data sent over the internet. It also happens to be one of the methods used in PGP and GPG programs. Unlike Triple DES, RSA is considered an asymmetric algorithm due to its use of a pair of keys. You’ve got your public key to encrypt the message and a private key to decrypt it. The result of RSA encryption is a huge batch of mumbo jumbo that takes attackers a lot of time and processing power to break.
- 4. Blowfish
Blowfish is yet another algorithm designed to replace DES. This symmetric cipher splits messages into blocks of 64 bits and encrypts them individually. Blowfish is known for its tremendous speed and overall effectiveness. Meanwhile, vendors have taken full advantage of its free availability in the public domain. You’ll find Blowfish in software categories ranging from e-commerce platforms for securing payments to password management tools, where it protects passwords. It’s one of the more flexible encryption methods available.
- 5. Twofish
Computer security expert Bruce Schneier is the mastermind behind Blowfish and its successor Twofish. Keys used in this algorithm may be up to 256 bits in length, and as a symmetric technique, you only need one key. Twofish is one of the fastest of its kind and ideal for use in hardware and software environments. Like Blowfish, Twofish is freely available to anyone who wants to use it.
If you’re wondering which type of encryption is better than the other, then there won’t be any clear winner as both symmetric and asymmetric encryption bring their advantages to the table, and we cannot choose only one at the expense of the other.
From the security perspective, asymmetric encryption is undoubtedly better as it ensures authentication and non-repudiation. However, the performance is also an aspect that we can’t afford to ignore, and that’s why symmetric encryption will always be needed.
Here’s the summary of what we hashed out for as far as types of encryption are concerned:
| Symmetric Encryption | Asymmetric Encryption |
| A single key is used to encrypt and decrypt data. | A key pair is used for encryption and decryption. These keys are known as public key and private key. |
| As it uses only one key, it’s a simpler method of encryption. | Thanks to the key pair, it’s a more complex process. |
| Symmetric encryption is primarily used for encryption. | Asymmetric encryption ensures encryption, authentication, and non-repudiation. |
| It provides faster performance and requires less computational power compared to asymmetric encryption. | It’s slower than symmetric encryption and requires higher computational power because of its complexity. |
| Smaller key lengths are used to encrypt the data (e.g., 128-256-bit length). | Usually, asymmetric encryption methods involve longer keys (e.g. 1024-4096-bit length). |
| Ideal for applications where a large amount of data needs to be encrypted. | Ideal for applications where a small amount of data is used by ensuring authentication. |
| Standard symmetric encryption algorithms include RC4, AES, DES, 3DES, and QUAD. | Standard asymmetric encryption algorithms include RSA, Diffie-Hellman, ECC, El Gamal, and DSA. |
Symmetric-key Cryptography
Symmetric key cryptography is a type of encryption scheme in which a similar key is used both to encrypt and decrypt messages. Such an approach of encoding data has been largely used in the previous decades to facilitate secret communication between governments and militaries.
Symmetric-key cryptography is called shared-key, secret-key, single-key, one-key, and eventually private-key cryptography. With this form of cryptography, it is clear that the key should be known to both the sender and the receiver that the shared. The complexity of this approach is the distribution of the key.
Symmetric key cryptography schemes are usually categorized such as stream ciphers or block ciphers. Stream ciphers work on a single bit (byte or computer word) at a time and execute some form of feedback structure so that the key is repeatedly changing.
A block cipher is so-called because the scheme encrypts one block of information at a time utilizing the same key on each block. In general, the same plaintext block will continually encrypt to the same ciphertext when using a similar key in a block cipher whereas the same plaintext will encrypt to different ciphertext in a stream cipher.
Block ciphers can operate in one of several modes which are as follows −
- Electronic Codebook (ECB) mode is the simplest application and the shared key can be used to encrypt the plaintext block to form a ciphertext block. There are two identical plaintext blocks will always create the same ciphertext block. Although this is the most common mode of block ciphers, it is affected to multiple brute-force attacks.
- Cipher Block Chaining (CBC) mode inserts a feedback structure to the encryption scheme. In CBC, the plaintext is exclusively-ORed (XORed) with the prior ciphertext block prior to encryption. In this mode, there are two identical blocks of plaintext not encrypted to a similar ciphertext.
- Cipher Feedback (CFB) mode is a block cipher implementation as a self-synchronizing stream cipher. CFB mode enables data to be encrypted in units lower than the block size, which can be beneficial in some applications including encrypting interactive terminal input. If it is using 1-byte CFB mode. Each incoming character is located in a shift register a similar size as the block, encrypted, and the block transmitted. At the receiving side, the ciphertext is decrypted and more bits in the block are discarded.
- Output Feedback (OFB) mode is a block cipher implementation conceptually same to a synchronous stream cipher. OFB avoids a similar plaintext block from making the same ciphertext block by using an internal feedback structure that is independent of both the plaintext and ciphertext bitstreams.
Public-key Cryptography
Public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the public key, available for anyone to use. The other key is known as the private key. Data encrypted with the public key can only be decrypted with the private key. Because of this use of two keys instead of one, public key cryptography is also known as asymmetric cryptography. It is widely used, especially for TLS/SSL, which makes HTTPS possible.
In cryptography, a key is a piece of information used for scrambling data so that it appears random; often it’s a large number, or string of numbers and letters. When unencrypted data, also called plaintext, is put into a cryptographic algorithm using the key, the plaintext comes out the other side as random-looking data. However, anyone with the right key for decrypting the data can put it back into plaintext form.
For example, suppose we take a plaintext message, “hello,” and encrypt it with a key; let’s say the key is “2jd8932kd8.” Encrypted with this key, our simple “hello” now reads “X5xJCSycg14=”, which seems like random garbage data. However, by decrypting it with that same key, we get “hello” back.
Plaintext + key = ciphertext: hello + 2jd8932kd8 = X5xJCSycg14=
Ciphertext + key = plaintext: X5xJCSycg14= + 2jd8932kd8 = hello
This is an example of symmetric cryptography, in which only one key is used. In public key cryptography, there would instead be two keys. The public key would encrypt the data, and the private key would decrypt it.
Public key cryptography is extremely useful for establishing secure communications over the Internet (via HTTPS). A website’s SSL/TLS certificate, which is shared publicly, contains the public key, and the private key is installed on the origin server — it’s “owned” by the website.
TLS handshakes use public key cryptography to authenticate the identity of the origin server, and to exchange data that is used for generating the session keys. A key exchange algorithm, such as RSA or Diffie-Hellman, uses the public-private key pair to agree upon session keys, which are used for symmetric encryption once the handshake is complete. Clients and servers are able to agree upon new session keys for each communication session, so that bad actors are unable to decrypt communications even if they identify or steal one of the session keys from a previous session.
Hash Functions
Hashing is the process of generating a value from a text or a list of numbers using a mathematical function known as a hash function.
A Hash Function is a function that converts a given numeric or alphanumeric key to a small practical integer value. The mapped integer value is used as an index in the hash table. In simple terms, a hash function maps a significant number or string to a small integer that can be used as the index in the hash table.
The pair is of the form (key, value), where for a given key, one can find a value using some kind of a “function” that maps keys to values. The key for a given object can be calculated using a function called a hash function. For example, given an array A, if i is the key, then we can find the value by simply looking up A[i].
At the heart of hashing is a mathematical function that operates on two fixed-size blocks of data to create a hash code. This hash function forms part of the hashing algorithm.
The size of each data block varies depending on the algorithm. Typically the block sizes are from 128 bits to 512 bits. The following illustration demonstrates the hash function −
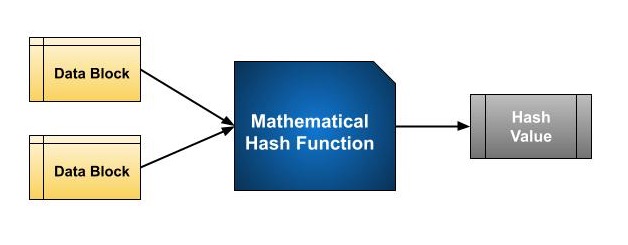
Hashing algorithm involves rounds of the above hash function like a block cipher. Each round takes an input of a fixed size, typically a combination of the most recent message block and the output of the last round.
This process is repeated for as many rounds as are required to hash the entire message. The schematic of the hashing algorithm is depicted in the following illustration −
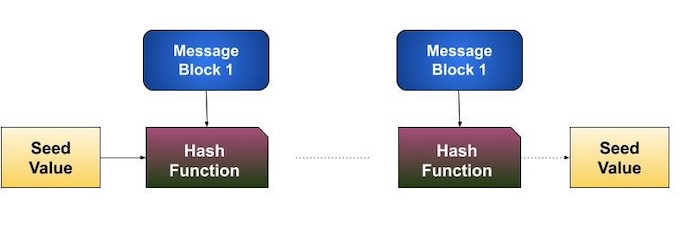
Since, the hash value of the first message block becomes an input to the second hash operation, the output of which alters the result of the third operation, and so on. This effect is known as the avalanche effect of hashing.
Avalanche effect results in substantially different hash values for two messages that differ by even a single bit of data.
Understand the difference between hash function and the algorithm correctly. The hash function generates a hash code by operating on two blocks of fixed-length binary data.
The hashing algorithm is a process for using the hash function, specifying how the message will be broken up and how the results from previous message blocks are chained together.
Hash functions are widely used in computer science and cryptography for a variety of purposes, including data integrity, digital signatures, password storage, and more.
There are many types of hash functions, each with its own strengths and weaknesses. Here are a few of the most common types:
1. SHA (Secure Hash Algorithm): SHA is a family of cryptographic hash functions designed by the National Security Agency (NSA) in the United States. The most widely used SHA algorithms are SHA-1, SHA-2, and SHA-3. Here’s a brief overview of each:
- SHA-1: SHA-1 is a 160-bit hash function that was widely used for digital signatures and other applications. However, it is no longer considered secure due to known vulnerabilities.
- SHA-2: SHA-2 is a family of hash functions that includes SHA-224, SHA-256, SHA-384, and SHA-512. These functions produce hash values of 224, 256, 384, and 512 bits, respectively. SHA-2 is widely used in security protocols such as SSL/TLS and is considered secure.
- SHA-3: SHA-3 is the latest member of the SHA family and was selected as the winner of the NIST hash function competition in 2012. It is designed to be faster and more secure than SHA-2 and produces hash values of 224, 256, 384, and 512 bits.
2. CRC (Cyclic Redundancy Check): CRC is a non-cryptographic hash function used primarily for error detection in data transmission. It is fast and efficient but is not suitable for security purposes. The basic idea behind CRC is to append a fixed-length check value, or checksum, to the end of a message. This checksum is calculated based on the contents of the message using a mathematical algorithm and is then transmitted along with the message.
When the message is received, the receiver can recalculate the checksum using the same algorithm, and compare it with the checksum transmitted with the message. If the two checksums match, the receiver can be reasonably certain that the message was not corrupted during transmission.
The specific algorithm used for CRC depends on the application and the desired level of error detection. Some common CRC algorithms include CRC-16, CRC-32, and CRC-CCITT.
3. MurmurHash: MurmurHash is a fast and efficient non-cryptographic hash function designed for use in hash tables and other data structures. It is not suitable for security purposes as it is vulnerable to collision attacks.
4. BLAKE2: BLAKE2 is a cryptographic hash function designed to be fast and secure. It is an improvement over the popular SHA-3 algorithm and is widely used in applications that require high-speed hashing, such as cryptocurrency mining.
BLAKE2 is available in two versions: BLAKE2b and BLAKE2s. BLAKE2b is optimized for 64-bit platforms and produces hash values of up to 512 bits, while BLAKE2s is optimized for 8- to 32-bit platforms and produces hash values of up to 256 bits.
5. Argon2: Argon2 is a memory-hard password hashing function designed to be resistant to brute-force attacks. It is widely used for password storage and is recommended by the Password Hashing Competition. The main goal of Argon2 is to make it difficult for attackers to crack passwords by using techniques such as brute force attacks or dictionary attacks. It achieves this by using a computationally-intensive algorithm that makes it difficult for attackers to perform large numbers of password guesses in a short amount of time.
Argon2 has several key features that make it a strong choice for password hashing and key derivation:
- Resistance to parallel attacks: Argon2 is designed to be resistant to parallel attacks, meaning that it is difficult for attackers to use multiple processing units, such as GPUs or ASICs, to speed up password cracking.
- Memory-hardness: Argon2 is designed to be memory-hard, meaning that it requires a large amount of memory to compute the hash function. This makes it more difficult for attackers to use specialized hardware to crack passwords.
- Customizable: Argon2 is highly customizable, and allows users to adjust parameters such as the memory usage, the number of iterations, and the output length to meet their specific security requirements.
Resistance to side-channel attacks: Argon2 is designed to be resistant to side-channel attacks, such as timing attacks or power analysis attacks, that could be used to extract information about the password being hashed.
6. MD5 (Message Digest 5): MD5 is a widely-used cryptographic hash function that produces a 128-bit hash value. It is fast and efficient but is no longer recommended for security purposes due to known vulnerabilities. The basic idea behind MD5 is to take an input message of any length, and produce a fixed-length output, known as the hash value or message digest. This hash value is unique to the input message, and is generated using a mathematical algorithm that involves a series of logical operations, such as bitwise operations, modular arithmetic, and logical functions.
MD5 is widely used in a variety of applications, including digital signatures, password storage, and data integrity checks. However, it has been shown to have weaknesses that make it vulnerable to attacks. In particular, it is possible to generate two different messages with the same MD5 hash value, a vulnerability known as a collision attack.
There are many other types of hash functions, each with its own unique features and applications. The choice of hash function depends on the specific requirements of the application, such as speed, security, and memory usage.


